Bottled Lightning: Creating an Industry-First Framework
How a side project turned into something I didn’t know the industry was missing.
I wasn't actively trying to invent something novel. I was tinkering with an idea that I'd been playing with for over a year off and on in my personal time. I've been reading O'Reilly textbooks on AI, ML, and data for the last few months. Somewhere along the way, I realized that I wasn't learning much from titles like "The Developer's Playbook for Large Language Model Security" by Steve Wilson.
That's when I started to wonder, am I closer to the edge of knowledge than I thought?
I wasn’t just reading about security, I was actively building it. I’ve been documenting prompt engineering techniques, playing with guardrails, and taking cutting-edge training around AI red teaming. Funnily enough, I didn't gain much from the AI red teaming training either, if I'm honest.
I realized early on that AI was the next wave, and my first thought coming from a security background was how do I contribute and get involved? The answer seemed obvious. I needed to help secure it and make it trustworthy.
Defensive security always lags behind offensive security, and I was determined to make sure that any systems I would use or deploy were systems that would do no harm. I saw guardrails and strategies for alignment, I saw filters and castle wall methodologies, but I did not see a full SecOps lifecycle enclosing the entire system anywhere.
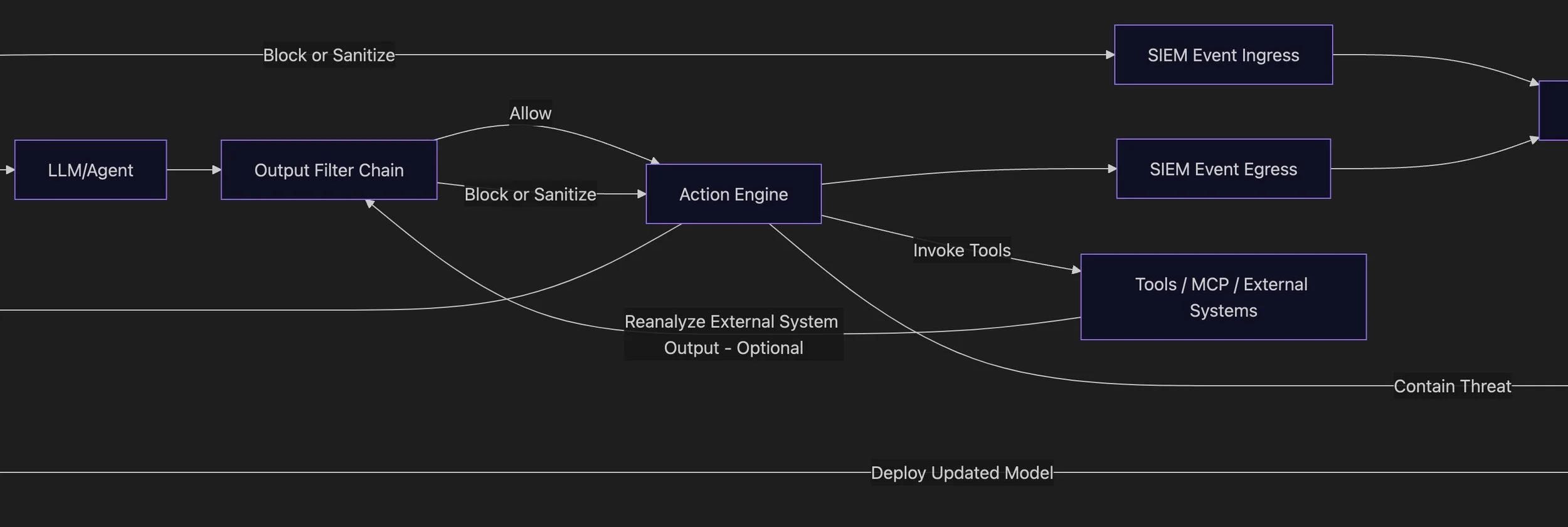
Nobody was thinking about Incident Response (IR). It was clear that the missing piece wasn’t another filter or alignment rule, but a true operational layer that could respond when things went wrong.
The seeds were sown for Prompt Injection Detection & Response: PIDR.
It started off as an idea. It began to take shape as a system. I built a prototype for an LLM security filter for a year-long AI/ML course through UC San Diego that informed some of the changes I needed for a more robust filter layer. By the time I was done with my prototype filter, I had the entire framework thought through, if only in my head.
It was when talking to a friend, a red teamer working internally at McDonald's Global, that it clicked that I had something serious. As I shared what I'd been toying with for a little over a year, what I'd built of it so far, and where I wanted to take it, I got a few unexpected responses.
A) He was significantly more impressed than I expected. I was comparing my prototype to the offering Meta (Facebook's parent company) built, LlamaGuard. He was comparing it to what most people understand how to build, as well as what people have built.
B) He told me I needed to keep my mouth shut about my idea until I filed a provisional patent at least.
I kinda blew it off a little. I couldn't quite believe that I was the one to come up with something totally new. Surely somebody else has built this. Somebody else has to have had this need. They would've built a framework around this for everyone to use already, right?
No. If anyone has built this, it is custom to the pipeline, internal, and no patents filed - at least that I'm able to find.
So here we are. Apparently, I'm an inventor.
I've worked on an industry-first tool before. I've come up with prompting techniques on my own that were "cutting-edge" publications within 2-3 weeks prior to me coming up with it naturally. I guess I really am closer to the edge of knowledge than I thought.
Sometimes you find something novel by just being thorough.
Read more about the Prompt Injection Detection & Response framework HERE.
PIDR Architecture
Snapshot of the data flow for PIDR